As the trucking industry becomes more connected through electric vehicles, telematics, data crunching, and more, fleets can't ignore the associated cyber risks.
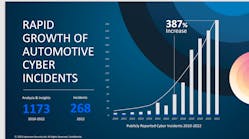
According to data acquired from Upstream, a cybersecurity and data analytics platform for connected vehicles, automotive cyber incidents have increased by 387% from 2017 to 2022. In 2022, 4% of those attacks were on EV charging equipment. This number is expected to climb with the continued shift toward electric vehicles.
The best way to mitigate cyber risks is to ensure privacy and security with fleet assets such as the connected vehicle and the chargers that power it, also known as electric vehicle supply equipment (EVSE). But that is easier said than done, considering the industry hasn't established EVSE privacy standards.
"There is currently no comprehensive EVSE cybersecurity approach, and limited best practices have been adopted by the EV/EVSE industry," according to a 2022 report by Sandia National Laboratories.
Passenger EVs, electric buses, and electric trucks have similar wireless charging communications paths—but none of them have guidance on the unique cybersecurity requirements specifically for wireless charging, according to a study by the U.S. Department of Transportation Volpe Center and Department of Energy Office of Policy.
See also: What will a national EV charging system look like?
Why EV security is a growing concern
ESVE systems provide electric power to the vehicle to recharge the vehicle's batteries. These systems include "electrical conductors, Battery Energy Storage Systems (BESS), software, and communications protocols that deliver energy efficiently and safely to the vehicle," according to the National Institute of Standards and Technology's Cybersecurity Framework Profile.
These systems cannot properly function without data communication. The Federal Energy Management Program outlined reasons ESVEs communicate with electric vehicles, such as helping provide power demand management and billing options. According to EV Adept, electric vehicles also communicate with chargers to send start/stop information, charging session status, and firmware update messages to the server.
Because EV charging stations require EV-to-charger and charger-to-grid connectivity, they can't function "off the grid," like diesel and other traditional fueling systems. Mayank Sharma, Schneider Electric X-to-Grid industrial affairs and standards manager, said in a recent webinar hosted by PTR, that because electric vehicle chargers are connected to a larger grid "ecosystem," any "miscalculation or any potential risk that can happen to a particular EV charging station can have a jeopardizing effect on the overall electricity infrastructure."
To imagine this "jeopardizing effect," think of the 2021 cyber attack on the Colonial Pipeline that led to some consumers filling plastic bags with gasoline, except this time, picture it happening to the electric power grid.
Not only is the larger electricity ecosystem at risk, but Sharma said the physical charging system is also at risk. A fleet customer could be denied charging, a hacker could control when a charger starts and stops charging or if it charges at all, and a consumer could charge their vehicle without paying.
See also: What fleets should know about cybersecurity
Avoiding charging cybersecurity vulnerabilities
Considering all this potential risk, damage, and danger, one might be hesitant to adopt EVs—but any vehicle connected to an app, SiriusXM, or a telematics system is vulnerable to cyber-attacks. The solution is to ensure the vehicles, both electric and ICE, and the fleet data systems and integrations, as well as ESVE, are protected.
As for EV chargers, in the same PTR webinar, Fabrice Roudet, energy transition general manager of Eaton Industries B.V., said once the charger manufacturer develops the charger, they cannot say, "OK, we did our part of the job, now it's up to the installer or the system integrators to do the rest."
He said if that were the case, there would be gaps and vulnerabilities in the charging infrastructure system, and that's why cybersecurity is critical across the board. Roudet said that if all parts of the system aren't working together—the charger manufacturers with the electricity provider, the OEM with the vehicle, the vehicle with the charger—the system will always have vulnerabilities.
Even the recent National Electric Vehicle Infrastructure Standards and Requirements rule by the Federal Highway Administration doesn’t fully address the problem, leaving EV charger cybersecurity up to the states.
Shira Sarid-Hausirer, vice president of marketing at Upstream, said the responsibility to ensure cybersecurity in the fleet space falls on both the vehicle manufacturer and the fleet. Yes, the vehicle OEM should ensure a safe vehicle, but the fleet owner who installs telematics and management systems must ensure the security of those systems as well.
The OEM is responsible because, Sarid-Hausirer said, as a fleet owner begins to understand the potential risk to their business, whether from an operational perspective or a data breach perspective, she expects to see fleets make cybersecurity part of their decision on which vehicle they choose to invest.
"Yes, they need to think about, very seriously, who they buy their fleet from," Sarid-Hausirer told FleetOwner, "and they need to do their research as to what are the cyber risks and compare them."
Once that decision is made, the fleet owner then becomes responsible. Sarid-Hausirer used a laptop as an example.
"It's kind of naïve to say that if you buy a laptop, you're not going to install an antivirus," she said. "The same goes to the fleet owners."
Fleets connect multiple systems to their vehicles, including telematics, aftermarket systems, driver-related apps, dispatcher apps, and more. "The vehicle has become a hub for technology," Sarid-Hausirer said. "It all has to be monitored. It all has to be protected, and it is the fleet owner's responsibility—just like they would protect their computers … These are essentially computers on wheels. They deserve and they require different layers of cybersecurity protection just like the IT systems of the world."
How can fleets shield themselves from cyberattacks?
This information seems daunting, and perhaps intimidating. But Sarid-Hausirer offered solutions through companies such as Upstream and others like it that have developed purpose-built solutions to help OEMs and fleet owners monitor their internal systems, their vehicles, and their applications for outside manipulation and help ensure quick remediation if manipulations or abnormalities are found.
Upstream in particular achieves this by ingesting fleet and vehicle data, analyzing the data, and developing the data's "digital twin," which is a snapshot of the vehicle's current state and its peripheral applications. Based on the digital twin, Upstream runs a set of detectors that look for anomalies that may indicate a potential security breach.
"We're looking for patterns, both expected or known vulnerabilities, but we also have a host of machine-learning and AI modules that look for stuff that we don't necessarily know that it's coming," Sarid-Hausirer said.
Once an anomaly is detected, an alert is sent to Upstream's office in Ann Arbor, Michigan, where a team of analysts determine if the anomaly is a threat. From there, the team connects directly with the fleet owner or OEM to help remediate the risk immediately.
But it's one thing to be reactive to a cybersecurity threat, and another thing to be proactive. To help fleets become proactive about these risks, Upstream provides a service called AutoThreat that continually searches the deep and dark web to look for vulnerabilities that are unknown to Upstream or the industry at large.
"What is the chatter of all these hackers in the dark web?" Sarid-Hausirer said. "What are they going after? So don't wait… Be smart about it. Do research and fix the vulnerabilities before they become real attacks."
One thing is certain, the automotive and trucking industry is currently undergoing a vast transformation of the digital and connected age. This fact is something to applaud and embrace, but the cybersecurity risks associated with this transformation cannot be ignored, especially by fleet owners whose business is at stake.
This article was originally published on FleetOwner.com.